Tech Talks
Here we discuss the latest tech, web trends and cyber insights.
Data Backup and Recovery
Data loss has devastating effects on any type or size business, often leading to massive financial losses. We accommodated data recovery services for Nashville for over twenty years. Let a CCI representative demonstrate to you the many optimal data backup and recovery services available to you.
Our Head is Not “in the Clouds”, but Our Business Is!
Are you looking for consulting for cloud services in Nashville? We will adapt your business operations to a cloud service that matches your requirements. Let a CCI representative advise you on all aspects of cloud services that will align with your goals.
Beware of the Cable Monster!
Are you searching for network cabling service in Middle TN? CCI will provide reliable and effective cabling solutions for your business. We will be glad to answer your cabling questions and schedule a time to set up your cabling system.
Cyber Security: Individual Accountability
We must vigilantly keep ourselves safe on the internet. It is important to recognize phishing emails characteristics. The sender's name may not reflect the email they are representing. There may be a suspicious button link hidden in the picture. We will assist you with identifying the common indicator of a phishing attempt. Please reach out to our expert consultants for solutions or questions.
Managed IT Services… What’s that?
Our proactive team will adapt to your IT needs and provide strategic plans to minimize your business’s computer-related disruptions. We offer a variety of services such as website design and hosting, help desk contracts, full security consultation, cabling, security camera installation, and much more. Partner with our managed IT Services in Nashville, we will optimize and support your IT needs.
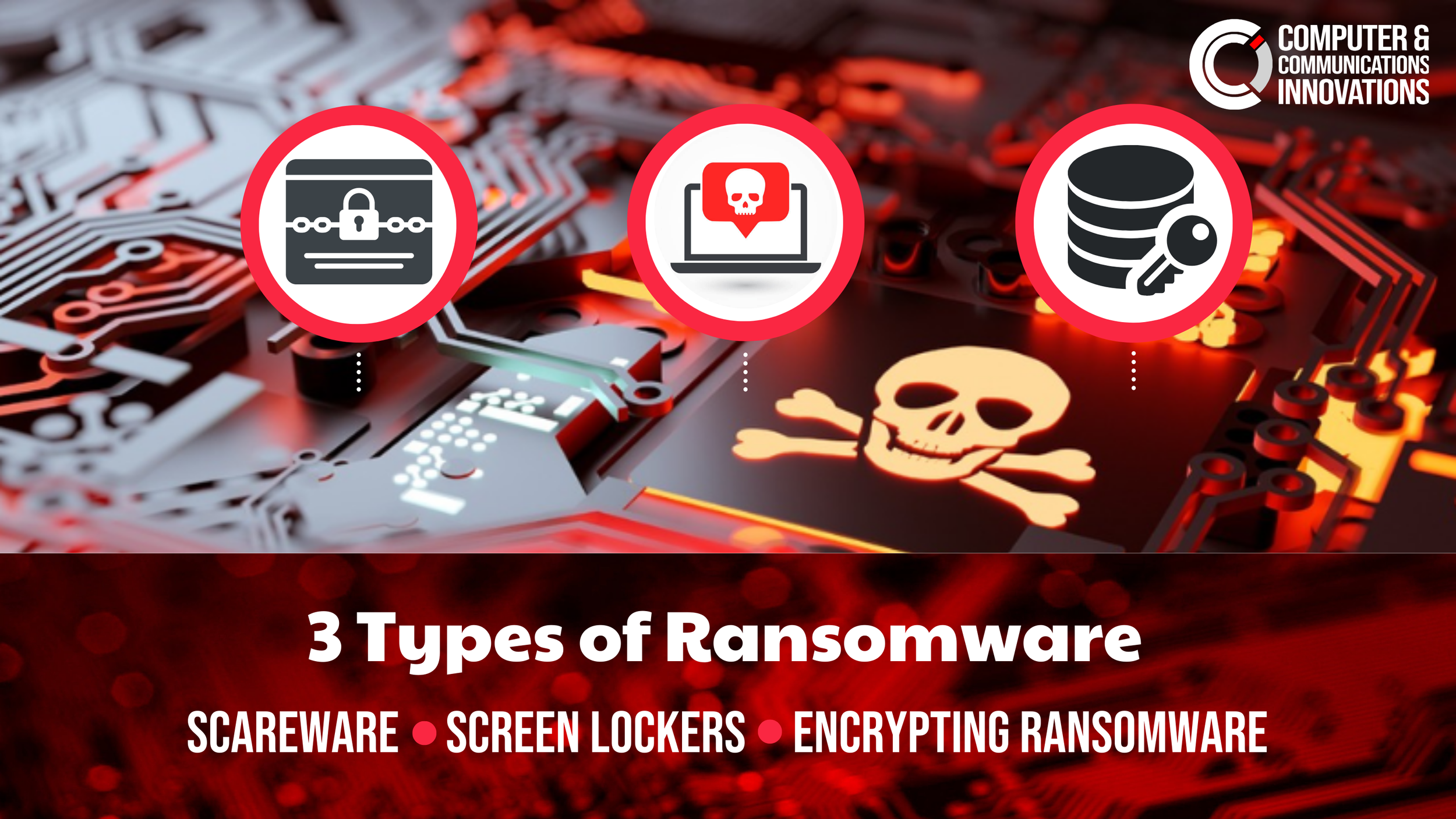
Ransom… where?
Ransomware is malware that causes computers to be inaccessible. The attacker may request you to contact a nonlegitimate IT technician and demand payment. Ransomware can be prevented by having reliable backups for your data. Contact our professional consultants to receive options for data backup and network malware protection solutions.
Time… The Final Frontier [in Business]
CCI offers internet connection monitoring services. We will alert you anytime your business's internet becomes unable 24/7. If your internet goes down, our team will assist you with getting your internet service up and running again.
Stop the Spam!
Spam takes up valuable time, e-mail inbox space, e-mail general storage space, and internet bandwidth. The CCI team will assist with managing your exchange server spam filter. Contact us today to schedule a consultation or for any questions.
Enhance Your Business with Security Cameras
Security cameras can deter crime, monitor customer behavior, and help identify areas to improve operations. We have installed security cameras in Nashville TN for several different businesses. Please contact us for any security system questions.
OMG...Where Did My Data Go?!
If your computer has died and gone on to a better place, there is no need to grieve over the loss of your data. Our Nashville Data Recovery experts will be able to retrieve all the information you had on your hard drive.
FBI found bot-collected personal info trading
The FBI recently seized Genesis Market’s domain and marketplace. This seizure led to the arrest of more than 120 people believed to be cybercriminals. To access this marketplace you had to be invited. Once invited, you could browse through an assortment of stolen data.
Business Intelligence automation
Help your business be more efficient and cut costs with SAW. We will help you build, manage, optimize, and make the most out of the business intelligent platforms that you are already paying for.
Tis The Season for Scams: How to Stay Safe Online for The Holidays
With December already in full swing, the rush for purchasing presents and sending email Christmas cards has begun. As the focus of shopping has shifted away from physical stores and into online websites and mobile apps, cybersecurity becomes more important than ever. We have collected some great tips from I.T Professionals to ensure that your private information isn’t a cybercriminal’s Christmas present!
Investment Scam Group CashRewindo Recycles Old Domains for New Schemes
A Cryptocurrency focused group of cybercriminals has recently created a unique method to bypass security tools, by hosting on domains years or even a decade old. This technique is referred to as Domain Aging, as security tools are more likely to overlook domains that have been online with no malicious content for longer than two years. By registering the domains years in advance, it becomes far more likely that the user is never warned that the site hosts malicious links or scams.
Utilize your Microsoft Subscription
Microsoft 365 is more than just Word or Excel on the go. This full-suite of cloud-based subscription service sets you up to achieve fearless business growth. The apps boost business productivity, facilitate better documentation, and expedite other management tasks. Let’s see how else Microsoft 365 benefits the business world:
How To Identify Spam Email
Spam Email Identification
Despite the commonality of phishing attacks (email-based), more than 80% of businesses fall for these deceptive tactics. Some emails look so authentic and compelling that it is easy to fall prey to the bait. And once you, a fish, get into the hacker’s net, your data and identity can be compromised in no time.
Ways to Identify Spam Emails
Phishing is a sophisticated cyberattack of netting users via email to obtain confidential information for ill purposes. These emails can 99% look like ones from your contacts. But the following distinguishes a bad email from a genuine one:
Malicious invoice emails compromises computers
Cybersecurity forms have reported a new iteration for trojan emotet malware. Hackers sent emails requesting payment or invoices. Users opened the excel or word document getting their computer infected by malware. Are you aware of your business security vulnerabilities? Contact CCI today for our cyber security audit services, we will check your network and provide custom security solutions.
Microsoft Doesn’t Call You Unsolicited
A hacker group sent invoice scam subscription pdfs with remote software attached. The hackers extracted their personal information and asked for money to not release their information. It is best to be cautious about unsolicited invoices. CCI offers secure email filtering and security services to ensure data is safeguarded. Contact us today for consultation or for any questions.
Windows Tips & Tricks You Should Be Using!
Learn some helpful, time saving tips for Windows users. The windows key shortcuts can save a ton of time if you know how to use them. Check the list of shortcuts for ones that can save you time! You will be able to maximize your time productivity by implementing these computer shortcut keys.
Security News- Android Exploit and MFA Fatigue
Android Lock-screen exploit found. Update your Android device to the latest version to protect your device. MFA fatigue allows users to access account protected by MFA by social engineering and sending several MFA requests until the user accepts the prompt. Data breaches continue to advance every day. Contact a CCI representative today for a security free consultation session.






![Time… The Final Frontier [in Business]](https://images.squarespace-cdn.com/content/v1/6363dd57e7e37c2da64faa0f/1682533281013-7WFDII4DHZ0H1VZHADCE/uptime.png)












